In the digital age, securing information is of utmost importance. With the increasing number of online services and the proliferation of data, protecting sensitive information from cyber threats has become a significant challenge. One of the most basic, yet persistent, methods that attackers use to gain unauthorized access to systems is the brute force attack. Despite being an unsophisticated technique, It continue to be a major threat due to their simplicity and effectiveness.
Table of Contents
What is a Brute Force Attack

A brute force attack is a trial-and-error method used to decode encrypted data such as passwords or cryptographic keys. The attacker systematically attempts all possible combinations of passwords or keys until the correct one is found. This method is straightforward but can be time-consuming and resource-intensive, depending on the complexity of the target.
Types of Brute Force Attacks
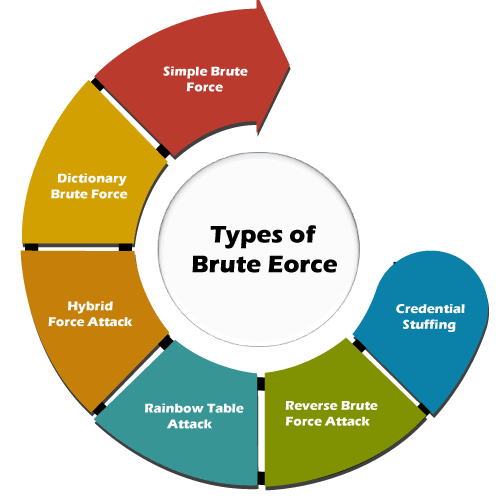
Simple Brute Force Attack:
- This is the most basic form, where the attacker tries every possible password combination without any optimization or strategy.
- Typically targets short and simple passwords.
Dictionary Attack:
- Utilizes a pre-arranged list of likely passwords and phrases, often sourced from previous data breaches.
- Reduces the number of attempts needed by guessing common passwords first.
Hybrid Brute Force Attack:
- Combines dictionary attacks with simple brute force methods.
- Starts with dictionary words and then appends numbers or symbols.
Reverse Brute Force Attack:
- Begins with a known password or a common password and tries it against multiple usernames.
- Often used against large user databases to find any accounts using weak passwords.
Credential Stuffing:
- Involves using known username-password pairs, typically obtained from data breaches.
- Exploits the tendency of users to reuse passwords across different services.
How Brute Force Attacks Work
The success of a brute force attack hinges on the computational power available to the attacker and the complexity of the password or encryption key being targeted. Here’s a simplified breakdown of how these attacks typically unfold:
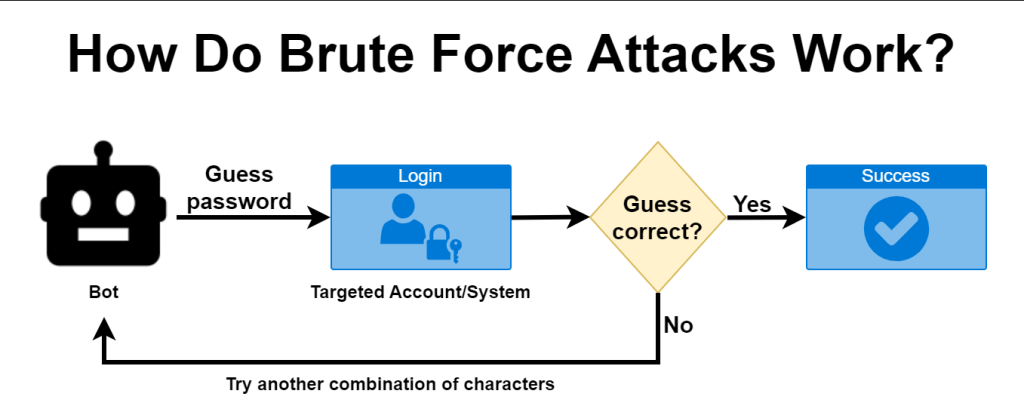
- Target Identification:
- The attacker selects a target, such as a login page, encrypted file, or database.
- Password Guessing:
- Using either a systematic approach or a dictionary list, the attacker begins guessing the password.
- Each guess is checked against the target to see if it unlocks access.
- Success or Failure:
- If the correct password is found, the attacker gains access.
- If not, the attack continues until either the correct password is found or countermeasures prevent further attempts.
Tools Used in Brute Force Attacks
Several tools are commonly used by attackers to automate:
- John the Ripper:
- A popular open-source password cracking tool.
- Combines different cracking modes and supports a variety of cryptographic hash functions.
- Hydra:
- Known for its speed and flexibility.
- Supports multiple protocols and allows parallel attacks.
- Aircrack-ng:
- Used primarily for cracking Wi-Fi passwords.
- Capable of recovering WEP and WPA-PSK keys.
- Hashcat:
- Advertised as the world’s fastest password recovery tool.
- Uses GPU acceleration to perform high-speed attacks on a wide range of hashing algorithms.
Impact of Brute Force Attacks
It can be devastating. Here are some potential consequences:
- Data Breach:
- Unauthorized access to sensitive information can lead to data breaches, compromising personal and financial data.
- Financial Loss:
- Businesses may incur significant costs due to fines, legal fees, and loss of customer trust.
- Service Disruption:
- An attacker gaining control of critical systems can disrupt services, causing downtime and operational losses.
- Reputation Damage:
- Public disclosure of security breaches can severely damage an organization’s reputation.
Mitigating Brute Force Attacks
It requires a multi-layered approach involving both technical and procedural measures. Here are some effective strategies:

- Strong Password Policies:
- Encourage the use of complex and unique passwords.
- Implement rules that require a mix of letters, numbers, and symbols.
- Account Lockout Mechanisms:
- Temporarily lock accounts after a certain number of failed login attempts.
- This can slow down attackers and alert administrators to potential attacks.
- Rate Limiting:
- Limit the number of login attempts from a single IP address over a specific period.
- Helps to prevent automated attacks.
- Two-Factor Authentication (2FA):
- Adds an additional layer of security by requiring a second form of verification.
- Even if the password is compromised, access is still restricted.
- CAPTCHA:
- Use CAPTCHA to distinguish between human users and automated scripts.
- Helps to prevent automated brute force attacks.
- Monitoring and Logging:
- Regularly monitor login attempts and account activity for unusual patterns.
- Maintain logs to investigate and respond to suspicious activity.
- Encryption:
- Ensure that sensitive data is encrypted both in transit and at rest.
- Use strong encryption algorithms and keep them up-to-date.
Real-World Examples of Brute Force Attacks

Deloitte (2017):
- Deloitte, one of the “Big Four” accounting firms, suffered a significant data breach due to a compromised administrator account.
- The breach was reportedly the result of a brute force attack on the company’s email platform.
Citrix (2019):
- Citrix Systems, a major provider of software solutions, was targeted in a brute force attack that compromised the personal information of employees and customers.
- The attackers used a combination of brute force and password spraying techniques.
Magento (2020):
- Thousands of Magento online stores were targeted in a large-scale attack.
- Attackers exploited weak passwords to gain administrative access and inject malicious scripts.
Future of Brute Force Attacks
As technology evolves, so do the methods used by attackers. While it may seem rudimentary, advancements in computational power and the proliferation of data breaches continue to make them a viable threat. Here are some trends and future considerations:
- Increased Automation:
- Attackers are leveraging machine learning and artificial intelligence to optimize it, making them faster and more efficient.
- Cloud Computing:
- Cloud services provide attackers with vast computational resources, enabling large-scale brute force attacks that were previously impractical.
- Quantum Computing:
- The advent of quantum computing poses a significant challenge to current cryptographic methods.
- Quantum computers could potentially crack complex passwords and encryption keys in a fraction of the time required by classical computers.
- Improved Defense Mechanisms:
- Advances in cybersecurity technologies, such as behavioral biometrics and AI-driven threat detection, are enhancing the ability to detect and mitigate it.
Conclusion
It despite their simplicity, remain a potent threat in the cybersecurity landscape. Understanding the mechanics, tools, and impacts of these attacks is crucial for developing effective defense strategies. By implementing robust security measures, staying informed about emerging threats, and continually updating defenses, organizations can significantly reduce the risk of falling victim to brute force attacks. The battle between attackers and defenders is ongoing, but with vigilance and proactive measures, the balance can be tipped in favor of security.

